A successful policy negotiation scheme for Policy-Based Management (PBM) has been implemented. Policy negotiation is the process of determining the “best” communication policy that all of the parties involved can agree on. Specifically, the problem is how to reconcile the various (and possibly conflicting) communication protocols used by different divisions. The solution must use protocols available to all parties involved, and should attempt to do so in the best way possible. Which protocols are commonly available, and what the definition of “best” is will be dependent on the parties involved and their individual communications priorities.
The network management and Web communication software used by the different organizations presents a stumbling block. Many of the tools used by the various divisions do not have the ability to communicate network management data with each other. At best, this means that manual human intervention into the communication protocols used at various network routers and endpoints is required. This process is tedious, error-prone, and slow.
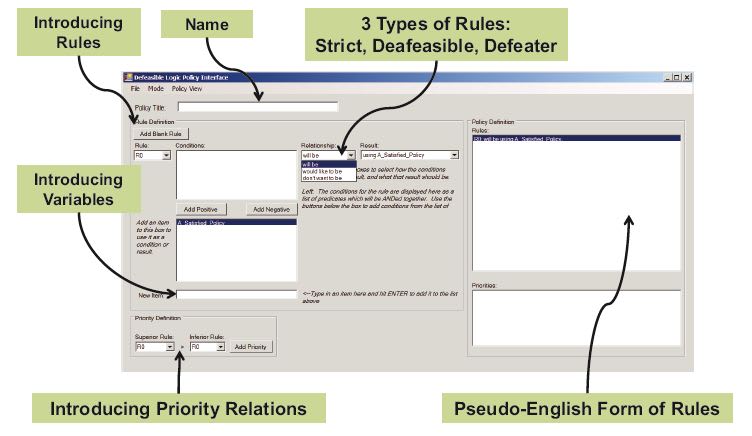
The present methods have inherent inefficiency and are not fully automatic, which heavily restricts their practical applications. The new method is based on an efficient algorithm. The new engine utilizes defeasible logic to describe communication policy constraints and priorities. Defeasible logic (see figure) is nonmonotonic, and contains three different types of rules: strict rules, which are strict “if/then” statements; defeasible rules that are “if this, then probably that” statements; and defeater rules that contradict the outcomes of defeasible rules.
The policy negotiation program reads in two files specifying the policies that the user wishes to combine, and outputs a single file describing the means of communication that satisfy both input policies, if any can be found.
To implement this method, a tool called DPC (Defeasible Policy Composition) was developed. To maintain that efficiency in the DPC tool, the data structures for the individual terms of each constraint are joined in linked-list fashion to their constraints and to a parent object representing each term. This can be visualized as a linked grid, where the heads of each column are the terms, the heads of each row are the rule names, and the body of the grid is the references to the terms that make up those rules. Each term reference is linked to its neighbors in the grid, which allows the algorithm to quickly and efficiently search through, add, and delete rows, terms, and individual term references.
This work was done by Farrokh Vatan and Edward T. Chow of Caltech for NASA’s Jet Propulsion Laboratory.
The software used in this innovation is available for commercial licensing. Please contact Daniel Broderick of the California Institute of Technology at
This Brief includes a Technical Support Package (TSP).

Policy-Based Negotiation Engine for Cross-Domain Interoperability
(reference NPO-48399) is currently available for download from the TSP library.
Don't have an account?
Overview
The document is a Technical Support Package for a Policy-Based Negotiation Engine aimed at enhancing cross-domain interoperability, developed under NASA's Commercial Technology Program. It outlines the challenges and objectives associated with managing complex mission tasks across different organizations, emphasizing the need for effective communication and collaboration.
The core of the document discusses the negotiation of IT security policies between two organizations, each with distinct requirements. Organization 1 mandates that all messages must include a security token and ensure integrity, accepting either an X.509 certificate or a combination of a SAML assertion and a username token. It specifies that messages signed with an X.509 certificate should use RSA signatures, while those with SAML assertions should use HMAC signatures. Importantly, both integrity algorithms cannot be used simultaneously, and the use of alternative authentication tokens is permitted only for mobile device access.
Conversely, Organization 2 requires messages to contain a security token and guarantee confidentiality. It accepts either an X.509 certificate or a combination of a SAML assertion and a username token, with the stipulation that if an X.509 certificate is used, SAML assertions should not be included. The confidentiality of messages must be ensured through encryption using either RSA or AES, and similar to Organization 1, multiple security tokens and confidentiality algorithms are not allowed. Additionally, all services must be accessible via mobile devices.
The document also describes a technical approach based on defeasible logic, which allows for efficient policy representation and negotiation. This method is computationally efficient, enabling linear time generation of conclusions, and models human reasoning, making it easier for policy designers to articulate their requirements. The syntax of defeasible logic facilitates the definition of alternative choices, conditional requirements, and prioritization of preferences, which are crucial for effective policy negotiation.
Finally, the structure of the negotiation tool is outlined, featuring a Defeasible Logic Engine that processes RuleML files representing various policies. The engine evaluates logical conclusions to determine if the criteria set by the policies are satisfied, ultimately leading to a final result.
Overall, the document serves as a comprehensive guide to the development and implementation of a negotiation engine that addresses the complexities of cross-organization IT security policy negotiation, fostering interoperability in diverse operational environments.

